Onion IRC is a education channel under #opNewBlood for Information Security education. The online course is available via IRC channel only on TOR which takes awhile to setup. Luckily we have a ready to use system Tails OS which can help us to on the IRC channel in a minute.
Tails OS is a packaged Linux that aims at preserving your privacy and anonymity. You can download the ISO here.
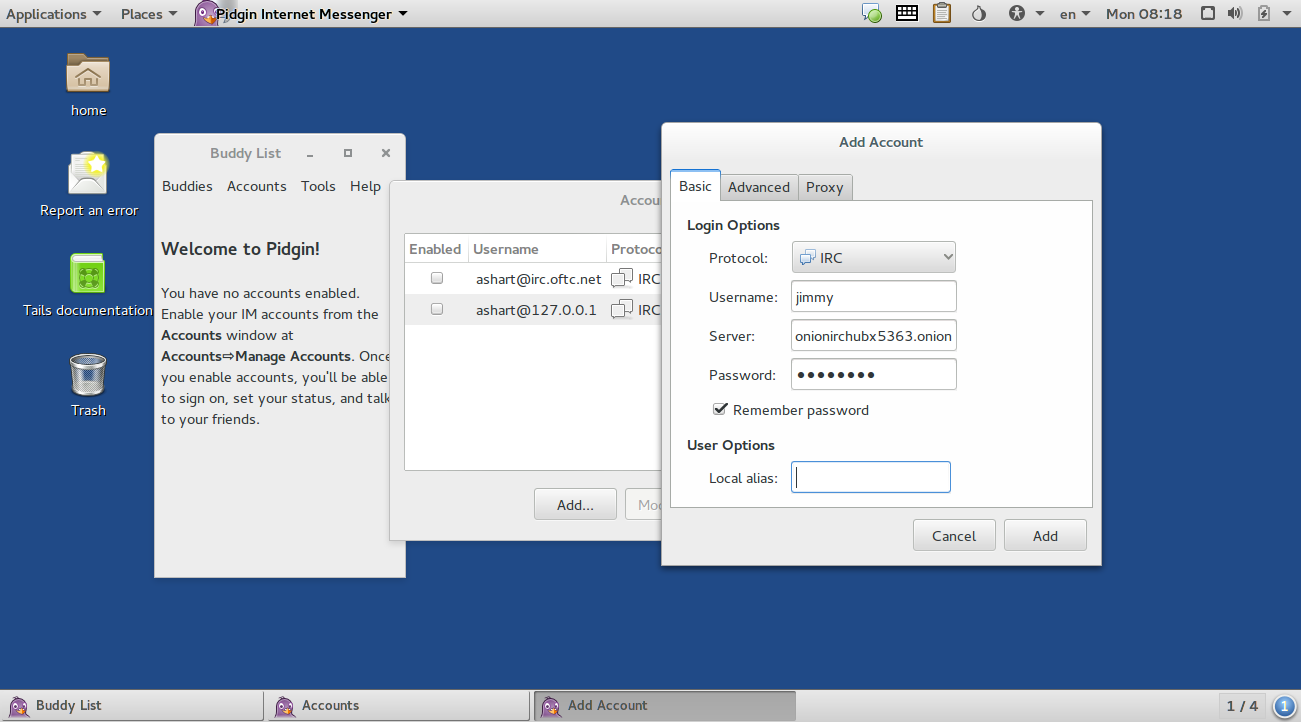
I use Virtual Box to build a VM, boot from the ISO image and then start connect to the IRC channel with Pidgin.
PS. My firewall doesn’t allow spoofing MAC Address, I cannot spoof it here.
Open Pidgin
onionirchubx5363.onion:6667
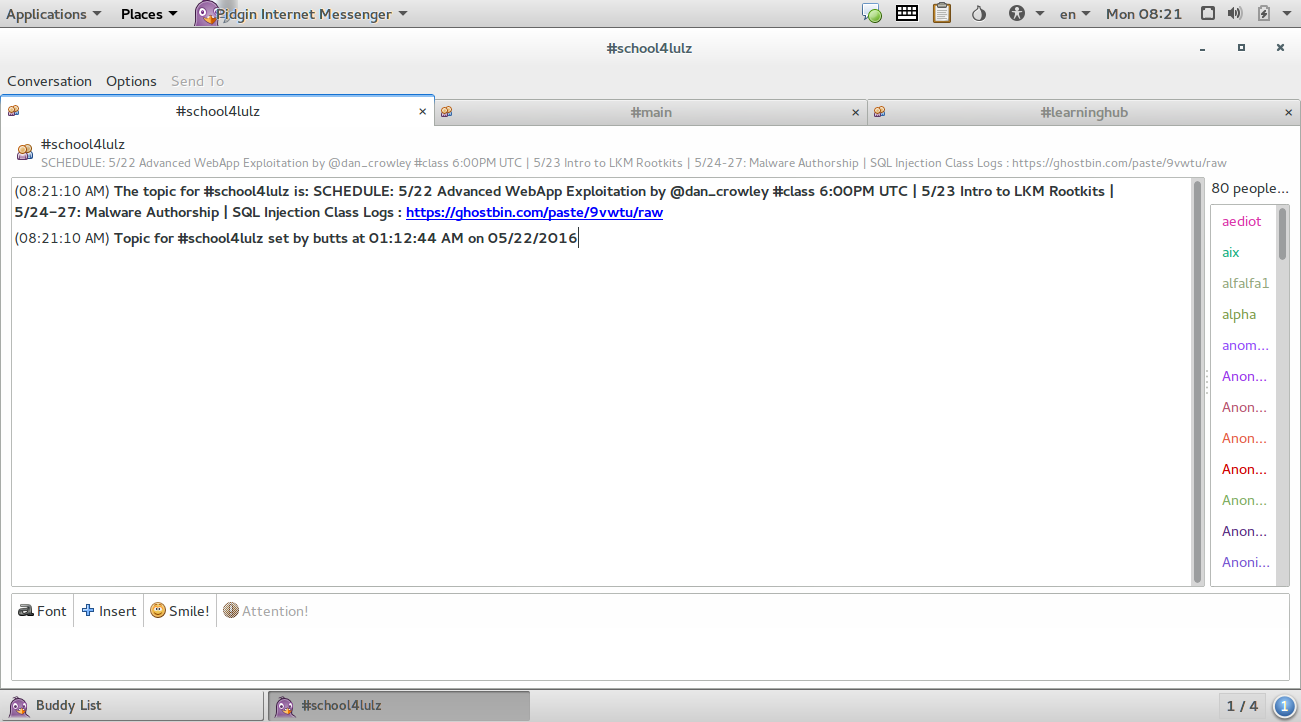
Type /list to list a list of chatrooms
#school4lulz , #main and #learninghub are popular channels.
You are done!